>”Chapter 2- METHODS OF DEFENCE”<
The advancement of Technology has made man dependent on Internet for all his needs.internet has given man easy access to everything while sitting at one place. Social networking, online shopping, storing data, gaming, online studying, online jobs, every possible thing that man can think of can be done through the medium of internet. Internet is used in almost every sphere. With the development of the internet and its related benefits also developed the concept of cyber crime. Cyber crimes are committed in different forms. A few years back, there was lack of awareness about the crimes that could be committed through internet. In the matters of cyber crimes,India is also not far behind the other countries where the rate of incidence of cyber crimes is also increasing day by day…
Essential components of the defence that must be present are a Firewall, Intrusion Detection Systems (IDS)/ Intrusion Prevention Systems (IPS), Unified Threat Management (UTM) and Antivirus.
ANTI-VIRUS

Mechanisms are put in place to limit the spread of Viruses and other malware. An antivirus system will function in conjunction with a firewall to check all incoming traffic for any viruses or malicious code. In addition, antivirus software can also be installed on individual servers (server-version) and host machines.
FIREWALL

Using a firewall physically and logically isolates the internal network form the external of any organization. The rules for the firewall are based on the explicit directions from the system administrator. All firewalls activities are logged and analyzed by the system administrator on a periodic basis. There is need to create firewall rules to allow a Computer to send to or receive traffic from programs, system services, computer or users. The rules can be configured to specify the Computer or users, program, service or port and protocol. You can specify which type of network adapter the rule will be applied to, such as Local Area network (LAN), wireless, remote access, virtual private network (VPN) connection or all types. You can also configure the rule to be applied when any profile is being used or only when a specified profile is being used. Rules can be created to take one of three actions for all connections that match the rule’s criteria:
*Allow the connection.
*Allow a connection only if it is secured through the use of Internet Protocol security (IPSec).
*Block the connection.
INTRUSION DETECTION SYSTEM (IDS)

Intrusion Detection Systems are put in place to passively monitor traffic by listening to and examining the packets entering or exiting a backbone/access network. They can monitor and analyze events that occur on a network or system, thus looking for intrusion attempts based on signatures or patterns. IDS require careful tuning to network conditions to be effective and make the system useful; otherwise false positives are too high.
INTRUSION PREVENTION SYSTEM (IPS)
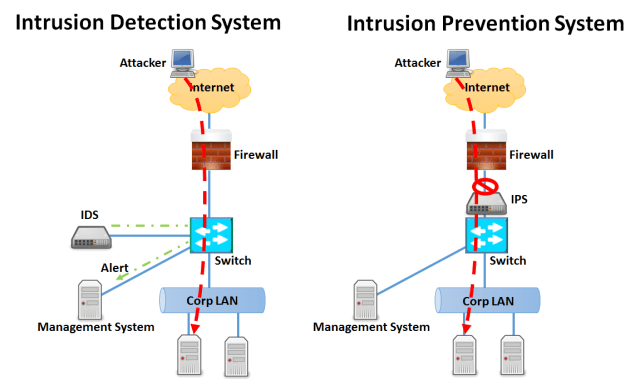
Intrusion Prevention Systems (IPS) is put in place to passively monitor traffic by listening to and examining the packets entering or exiting a backbone/access network. It is any device (hardware or software) that has the ability to detect attacks, both known and unknown and prevents the attack from being successful.
UNIFIED THREAT MANAGEMENT (UTM)
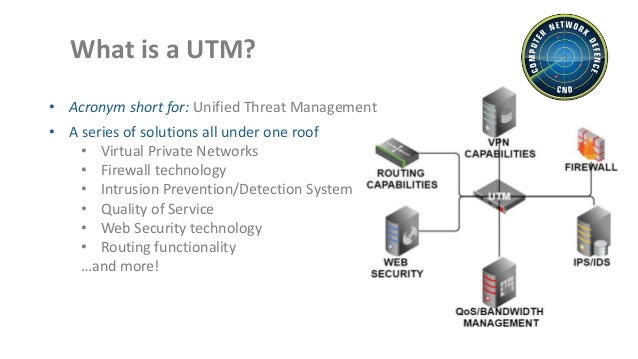
Unified Threat Management Systems are put in place to passively monitor traffic by listening to and examining the packets entering or exiting a backbone/access network. It has some advanced features such as URL and keyword filtering.”
Related Link>>Also check
Computer Threats
History of Computer
Technology
Internet
Top 10 Windows Tool
Computer Threats
