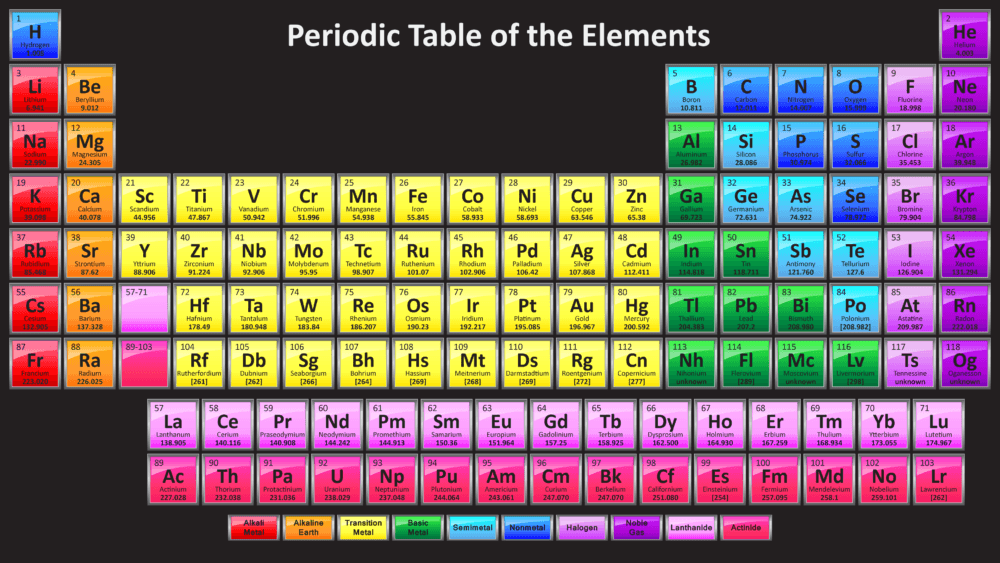
List of all Synthetic Elements till 2022
What are Synthetic Elements (man-made)? Synthetic elements are unstable Chemical elements and are not naturally found on the earth. These elements are synthesized (made)in the laboratory. They are unstable and … Read more